This blog is the second in a series that looks at a NIST project “Addressing Visibility Challenges with TLS 1.3 within the Enterprise.” The home page for the project is here: https://www.nccoe.nist.gov/addressing-visibility-challenges-tls-13. The NIST site includes details of the project and organizations involved in the project as well as drafts of the project documents which will be updated as the project progresses.
As detailed in Part 1, the NIST project is looking at two passive decryption mechanisms that can be used within an enterprise data center to gain visibility into TLS 1.3 traffic. In this post, we look at the first of these techniques: Bounded lifetime Diffie-Hellman key pairs.
In order to understand how this technique works, we first need to look at how the TLS handshake works in TLS 1.3 and how it provides Perfect Forward Secrecy (PFS). The normal handshake uses Ephemeral Diffie-Hellman key exchange between TLS client and server to produce an ephemeral key (symmetric key) which client and server then use to encrypt TLS records. During the handshake, both client and server generate unique values that are used to create the unique ephemeral key. As the unique values are not exchanged over the wire between client and server, they cannot be observed by a passive decrypt device, preventing such a device from figuring out what the resultant ephemeral key is. This mechanism ensures that every TLS 1.3 session terminating on an enterprise server has a unique ephemeral key. In addition, even if the TLS server is compromised and its certificate and private key are acquired, it is impossible to determine what they ephemeral key was for a previously captured TLS flow.
So, a regular TLS 1.3 flow benefits from PFS and this means that passive decryption is impossible and that any captured TLS flows that occurred prior to a TLS server being compromised cannot be decrypted. The only way to gain visibility into the flow is using a B&I technique as described in part one of the blog series.
Bounded lifetime Diffie-Hellman key pairs allow for passive decryption but do result in a reduction in PFS as will be explained later. Instead of the TLS server generating a unique value to be used in a TLS handshake, it is provisioned with a static Diffie-Hellman key pair and these are for all TLS handshakes during a window of time (the lifetime). If a passive decryption device knows the static Diffie-Hellman key pair being used by the server, then it has sufficient information to figure out the ephemeral key that results from the handshake without needing to be in-line. Each TLS flow will still have a unique ephemeral key as the random element that the client generates will be different for every flow.
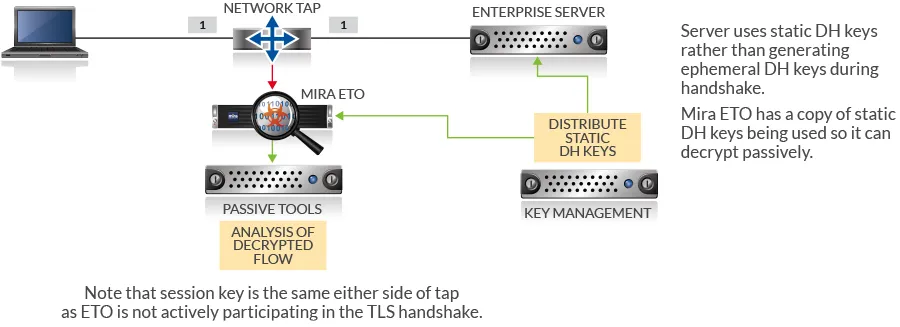
In order for this mechanism to work, a key management system is required which can provision the static Diffie-Hellman key pairs to the server and to the passive decryption device. The key management system determines the “lifetime” of the key pair and ensures that replacement key pairs are provisioned to the server and passive decrypt device before the pair in use expire. The key management system can also retain details as to which static key pair was in use at what time, allowing post-facto decryption of a captured flow in addition to the realtime decryption being done by the passive decryption device.
As noted earlier, TLS 1.3 PFS prevents post-facto decryption of a captured flow that occurred before the TLS server was compromised. We can see that this is no longer true in the bounded lifetime static Diffie-Hellman key case as compromising the server and acquiring the static key pair will allow decryption of any already captured TLS flows that were established during the time window during which the static key pair were in use. While this does weaken PFS, it may be acceptable as long as the rotation period for the static key pair is small. Compared to the situation with earlier versions of TLS where compromising the server and acquiring the certificate and keys allowed post-facto decryption of all flows to that server since the certificate was installed, the bounded lifetime approach significantly reduces the consequence of server compromise.
The diagram below shows the elements involved in implementing a bounded lifetime Diffie-Hellman key pair mechanism. Mira’s ETO can receive bounded lifetime key pairs from the key management system and use these to carry out passive realtime decryption of TLS 1.3 flows.
Bounded lifetime Diffie-Hellman key pair mechanism
In the post-facto decryption case, the key management system needs to retain the key pairs and be able to provide them to a decryption device when requested at some time in the future. The decryption device will need to know when a captured flow occurred in order to request the appropriate key pair from the key management system in order to decrypt the flow. Clearly, the key management system needs to provide secure storage for the rotated key pairs and have strong access controls over who can access the key pairs.
About the Author
David Wells is a seasoned product strategist and entrepreneur with a career spanning over three decades in technology, networking and cybersecurity. Currently, he collaborates with Mira Security to deliver industry-leading encrypted traffic visibility solutions, while also running his consultancy, Glen Tech, where he advises global tech companies and supports local businesses in Ireland.
David has held prominent leadership roles, including VP of Product Management at Blue Coat Systems (later acquired by Symantec) and founder of Netronome Systems, where he contributed significantly to advancements in SSL technology and enterprise security. His expertise extends to corporate strategy, R&D, mergers and acquisitions, and technology marketing, with impactful tenures at Marconi PLC, Tellabs and Netcomm Ltd.
Now based in County Kerry, Ireland, David combines his professional expertise with personal passions like boating, blending innovation with community involvement. His career is marked by a commitment to driving technological progress and empowering both enterprises and local communities.